Phishing and smishing
Schützen Sie sich vor PhishingHier finden Sie Ressourcen, um sich vor Versuchen des Social Engineerings zu schützen. Lernen Sie Folgendes kennen:
Arten von Social Engineering
Worauf Sie bei einer Phishing-E-Mail achten müssen
Worauf Sie bei einer Smishing-Textnachricht achten müssen
Best Practices für die Cybersicherheit
Ressourcen zum Schutz vor Phishing
Types of social engineering
Phishing
Phishing is an email-based type of online fraud designed to steal your personal information such as credentials (account name & password), credit card/bank account information, or other valuable related data. Phishing is typically carried out by e-mail and is disguised to appear as a legitimate request from someone you think you can trust. The sender places links, attachments, and phone numbers in these messages intended to get you to respond; this often results in malware downloading to personal devices, re-directs to phony websites, or direct phone calls with scammers who in turn steal and commit fraud with your identity.
Smishing
Also known as SMS (text), phishing is a type of fraud performed on cellular phones and smart devices that is designed to steal your personal information or compromise your device. Much like phishing, it is also disguised to appear as a legitimate text message from someone you think you can trust. The sender places links, attachments, and phone numbers in these messages intended to get you to respond; this often results in malware downloading to personal devices, re-directs to phony websites or direct phone calls with scammers who in turn steal and commit fraud with your identity.
If you suspect that you received a smishing text, report the number to your phone provider, block the sender, and delete the message.
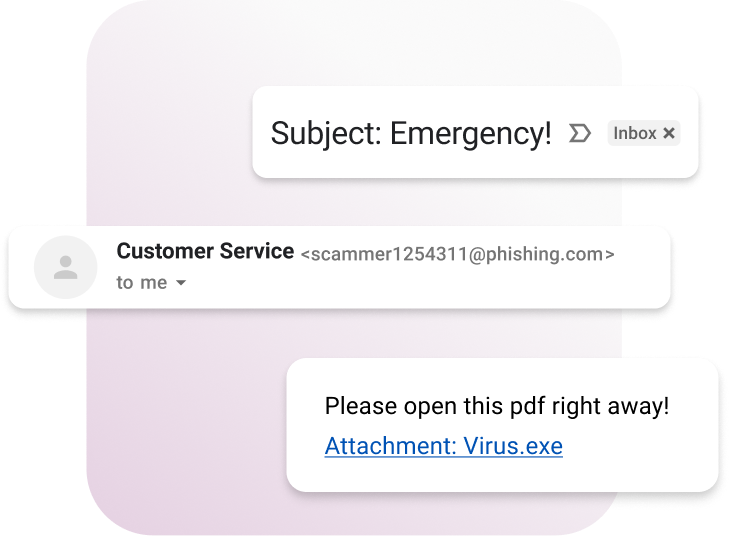
What to look for in a phishing e-mail
Mismatched email domain:
URL link mismatch to supposed sender domain.
Encrypted, compressed, or executable files:
Examples: [.7z, exe., bat, bin, rar, -py]
Note: Some mail browsers may block or warn if these are seen as attachments. If you aren't expecting an email with an attachment, beware.
Sounds urgent, bad spelling/grammar, makes you nervous:
Phishing emails are written to be enticing, eye catching, and will try to get you to act now.
If you didn't expect an email, and something doesn't “smell” right, chances are it's phishing!
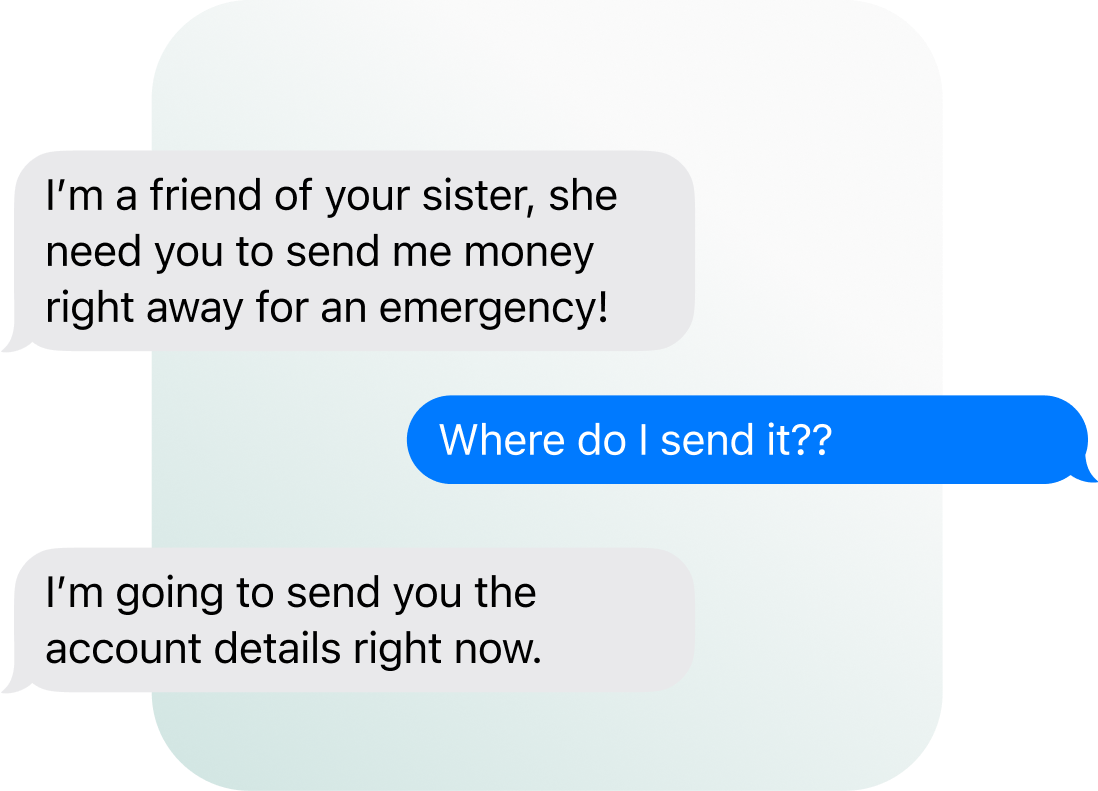
What to look for in a Smishing text
If you get a text from an unknown number:
Does the text feel highly unexpected and unusual?
If the person says they know you, how else can you verify them (e.g., email, another phone number you have for them, or through social media)?
Were you expecting a text regarding the subject?
Is the sender asking for personal information or for you to do something “urgent?”
Does the text contain an unusual looking link the sender wants you to click? If any of the above apply, chances are it's smishing.
Cybersecurity best practices
On average, identity theft and personal data breaches occur over 100,000 times a year in the United States, according to the Federal Bureau of Investigation (FBI). Many data breaches result in the compromise of login credentials, credit card/bank account information, and sensitive identification numbers like social security numbers.
Cybersecurity dos
Use credit monitoring services or freeze your credit with the credit bureaus.
Enable Multi-factor Authentication (MFA) on all accounts for financial services.
Monitor banking and credit card accounts daily for unusual purchases.
Monitor email and text message for alerts of successful and failed logons as well as notifications of purchases.
Use unique passwords for important web sites. A password manager is a great way to do this.
Use complex/long passwords more than 12 characters including a mix of uppercase, numbers, and special characters).
Ensure online sessions are secure before entering any financial information (look for the lock or HTTPS in the browser URL).
Cybersecurity don’ts
Use credit monitoring services or freeze your credit with the credit bureaus.
Enable Multi-factor Authentication (MFA) on all accounts for financial services.
Monitor banking and credit card accounts daily for unusual purchases.
Monitor email and text message for alerts of successful and failed logons as well as notifications of purchases.
Use unique passwords for important web sites. A password manager is a great way to do this.
Use complex/long passwords more than 12 characters including a mix of uppercase, numbers, and special characters).
Ensure online sessions are secure before entering any financial information (look for the lock or HTTPS in the browser URL).
Hilfreiche Ressourcen
Schützen Sie sich mit MFA vor Hackern
So erkennen Sie Phishing-Versuche per E-Mail
Alle Informationen sind auf Englisch.

Glauben Sie, dass Sie Opfer eines Betrugs geworden sind? Lassen Sie uns Ihnen helfen.
Glauben Sie, dass Sie Opfer eines Betrugs geworden sind? Lassen Sie uns Ihnen helfen.
Falls Sie glauben, dass Sie Opfer eines Betrugs geworden sind, füllen Sie bitte unser Formular zum Online-Melden von Betrug aus.
Wenn Sie bei einer noch nicht eingegangenen Transaktion einen Betrug vermuten, wenden Sie sich bitte an unser Kundendienstzentrum, um die Transaktion umgehend stornieren zu lassen.
Wenn Sie MoneyGram zum Überweisen von Geld aufgrund eines Betrugs genutzt haben, füllen Sie bitte unser Formular aus, um den Betrug online zu melden.